Rsa Securid Client For Mac
Introduction
This document describes how to configure a Cisco IOS® device to authenticate AnyConnect clients with One Time Passwords (OTPs) and the use of a Rivest-Shamir-Addleman (RSA) SecurID server.
I have Windows, Mac, and Linux computers; but I am only able to connect to some of my company's websites through the Windows and Mac machines at the moment because they are the only ones with RSA SecurID software tokens. RSA SecurID Software Token for Windows Phone is available free of charge through the Windows Phone Store. Search for 'SecurID' oin the 'Business' category. Token seeds are available through RSA sales channels. Horizon Client for Mac also supports optional RADIUS and RSA SecurID authentication. What's New in This Release. For example, if you connect a USB headset to the Mac client system during a remote desktop session and you want to use that headset on the remote desktop, you must disconnect and reconnect to the remote desktop.

Note: OTP authentication does not work on Cisco IOS versions that have the fix for the enhancement requests CSCsw95673 and CSCue13902.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- RSA SecurID server setup
- SSLVPN configuration on the Cisco IOS headend
- Web-VPN
Components Used
The information in this document is based on these software and hardware versions:
- CISCO2951/K9
- Cisco IOS Software, C2951 Software (C2951-UNIVERSALK9-M), Version 15.2(4)M4, RELEASE SOFTWARE (fc1)
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
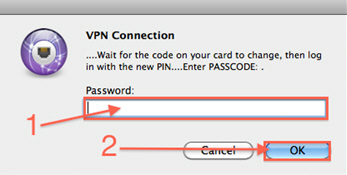
Although the AnyConnect client has always supported OTP-based authentication, prior to the fix for Cisco bug ID CSCsw95673, the Cisco IOS headend did not process RADIUS Access-Challenge messages. After the initial login prompt (where users enter their 'permanent' usernames and passwords), RADIUS sends the 'Access-Challenge' message to the Cisco IOS gateway, which asks users to enter their OTP:
At this point, the AnyConnect client is expected to show an additional pop-up window that requests users for their OTP, but since the Cisco IOS device did not process the Access-Challenge message, this never happens and the client sits idle until the connection times out.
However, as of Version15.2(4)M4, Cisco IOS devices should be able to process the challenge-based authentication mechanism.
Configure
Network Diagram
One of the differences between the Adaptive Security Appliance (ASA) and Cisco IOS headends is that Cisco IOS Router/switches/Access Points (APs) only support RADIUS and TACACS. They do not support the RSA-proprietary protocol SDI. The RSA server however supports both SDI and RADIUS. Therefore, in order to use OTP authentication on a Cisco IOS headend, the Cisco IOS device must be configured for RADIUS protocol and the RSA server as a RADIUS token server.
Note: For more details about the differences between RADIUS and SDI, refer to the Theory section of RSA Token Server and SDI Protocol Usage for ASA and ACS. If SDI is required, then an ASA must be used.
Note: Use the Command Lookup Tool (registered customers only) in order to obtain more information on the commands used in this section.
- Configure the authentication method and the Authentication, Authorization, and Accounting (AAA) server group:
- Configure the RADIUS server:
- Configure the router to act as an Secure Sockets Layer VPN (SSLVPN) server:
Note: For more a detailed configuration guide on how to set up SSLVPN on a Cisco IOS device, refer to AnyConnect VPN (SSL) Client on IOS Router with CCP Configuration Example.
Verify
There is currently no verification procedure available for this configuration.
Troubleshoot
In order to troubleshoot the entire authentication process for an incoming AnyConnect client connection, you can use these debugs:
- debug radius authentication
- debug aaa authentication
- debug webvpn authentication
The Output Interpreter Tool (registered customers only) supports certain show commands. Use the Output Interpreter Tool in order to view an analysis of show command output.
Note: Refer to Important Information on Debug Commands before you use debug commands.
Introduction
This document describes how to configure a Cisco IOS® device to authenticate AnyConnect clients with One Time Passwords (OTPs) and the use of a Rivest-Shamir-Addleman (RSA) SecurID server.
Note: OTP authentication does not work on Cisco IOS versions that have the fix for the enhancement requests CSCsw95673 and CSCue13902.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- RSA SecurID server setup
- SSLVPN configuration on the Cisco IOS headend
- Web-VPN
Components Used
Download Rsa Securid Windows
The information in this document is based on these software and hardware versions:
Rsa Securid How To Use
- CISCO2951/K9
- Cisco IOS Software, C2951 Software (C2951-UNIVERSALK9-M), Version 15.2(4)M4, RELEASE SOFTWARE (fc1)
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Background Information
Although the AnyConnect client has always supported OTP-based authentication, prior to the fix for Cisco bug ID CSCsw95673, the Cisco IOS headend did not process RADIUS Access-Challenge messages. After the initial login prompt (where users enter their 'permanent' usernames and passwords), RADIUS sends the 'Access-Challenge' message to the Cisco IOS gateway, which asks users to enter their OTP:
At this point, the AnyConnect client is expected to show an additional pop-up window that requests users for their OTP, but since the Cisco IOS device did not process the Access-Challenge message, this never happens and the client sits idle until the connection times out.
However, as of Version15.2(4)M4, Cisco IOS devices should be able to process the challenge-based authentication mechanism.
Configure
Network Diagram
One of the differences between the Adaptive Security Appliance (ASA) and Cisco IOS headends is that Cisco IOS Router/switches/Access Points (APs) only support RADIUS and TACACS. They do not support the RSA-proprietary protocol SDI. The RSA server however supports both SDI and RADIUS. Therefore, in order to use OTP authentication on a Cisco IOS headend, the Cisco IOS device must be configured for RADIUS protocol and the RSA server as a RADIUS token server.
Note: For more details about the differences between RADIUS and SDI, refer to the Theory section of RSA Token Server and SDI Protocol Usage for ASA and ACS. If SDI is required, then an ASA must be used.
Note: Use the Command Lookup Tool (registered customers only) in order to obtain more information on the commands used in this section.
- Configure the authentication method and the Authentication, Authorization, and Accounting (AAA) server group:
- Configure the RADIUS server:
- Configure the router to act as an Secure Sockets Layer VPN (SSLVPN) server:
Note: For more a detailed configuration guide on how to set up SSLVPN on a Cisco IOS device, refer to AnyConnect VPN (SSL) Client on IOS Router with CCP Configuration Example.
Verify
There is currently no verification procedure available for this configuration.
Troubleshoot
In order to troubleshoot the entire authentication process for an incoming AnyConnect client connection, you can use these debugs:
- debug radius authentication
- debug aaa authentication
- debug webvpn authentication
The Output Interpreter Tool (registered customers only) supports certain show commands. Use the Output Interpreter Tool in order to view an analysis of show command output.
Note: Refer to Important Information on Debug Commands before you use debug commands.